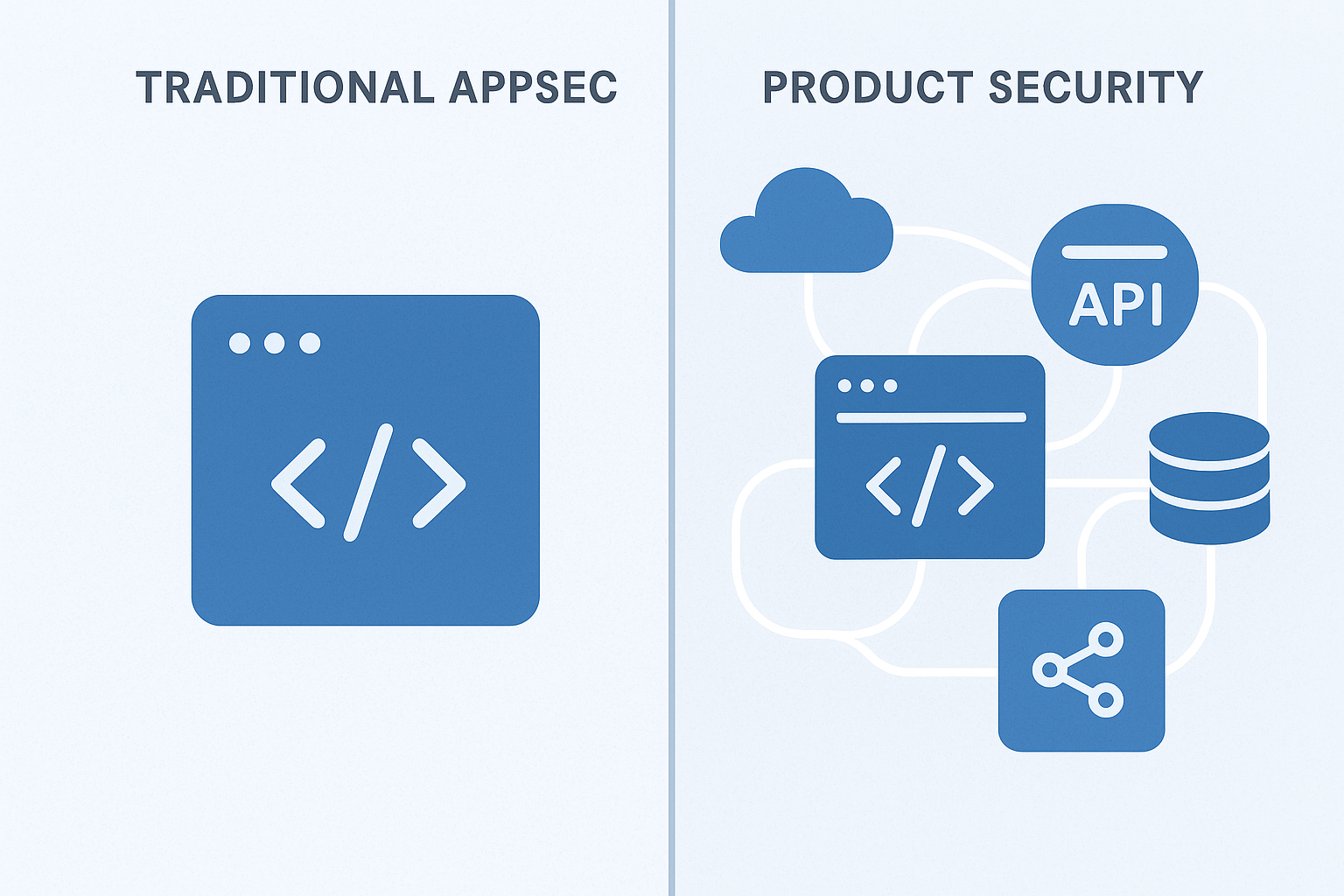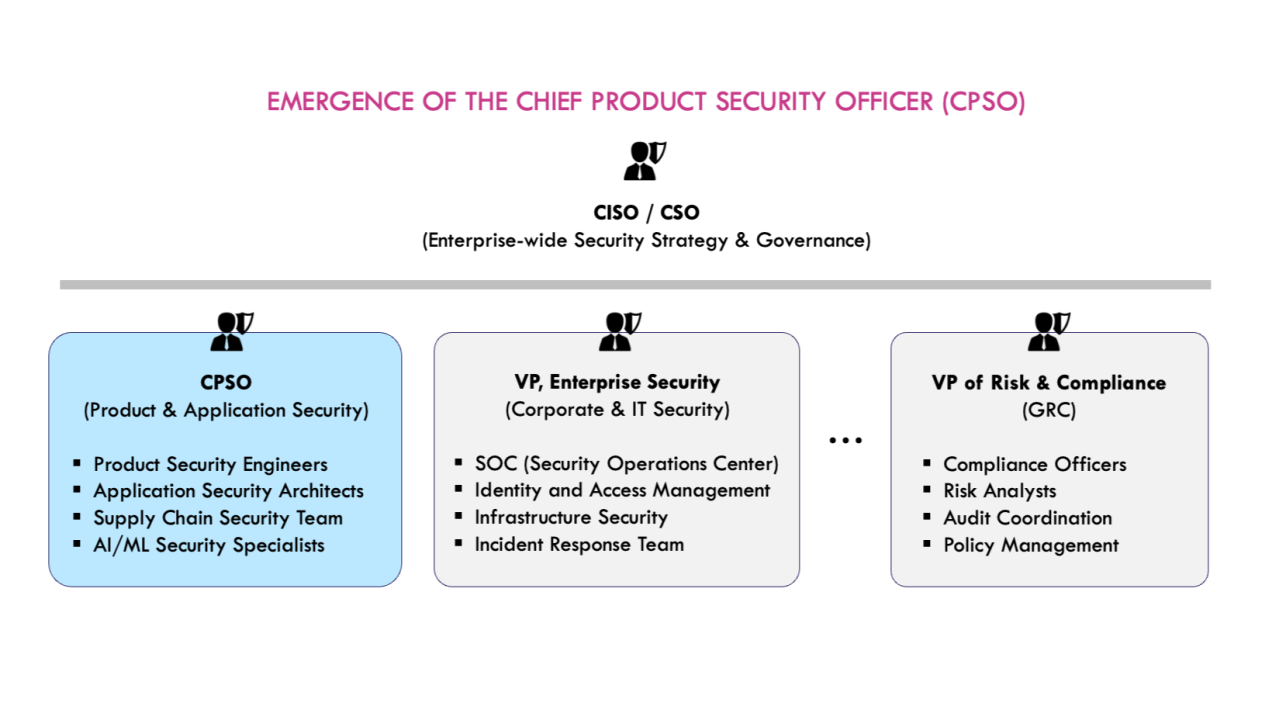
Emergence of the Chief Product Security Officer (CPSO) in the AI-Native Era
As applications evolve into AI-native products with agentic development, CSOs and CISOs are fundamentally rethinking their organizational structure. The Chief Product Security Officer represents this critical evolution.