· Appaxon Team · insights · 3 min read
What is BAS (Breach & Attack Simulation)?
Breach & Attack Simulation (BAS) is a cybersecurity approach that uses automated tools to continuously simulate real-world cyberattacks against an organization's security infrastructure.
Breach & Attack Simulation (BAS) is a cybersecurity approach that uses automated tools to continuously simulate real-world cyberattacks against an organization’s security infrastructure. Unlike traditional penetration testing or red teaming that performs attacks on real environments, BAS platforms run attack scenarios that replicate the tactics, techniques, and procedures used by actual threat actors. These simulations test an organization’s security controls, detection capabilities, and incident response processes without causing damage to systems or disrupting business operations.
Framework Integration and Attack Coverage
BAS platforms typically integrate with the MITRE ATT&CK framework to execute comprehensive attack scenarios that span the entire cyber kill chain—from initial reconnaissance and lateral movement to data exfiltration and persistence. The simulations can target various attack vectors including email-based threats, network vulnerabilities, endpoint weaknesses, and web application exploits.
Most BAS solutions provide both agent-based testing (using software installed on internal systems) and agentless testing (external scanning and simulation) to evaluate security from multiple perspectives.
Continuous Security Validation
The primary value of BAS lies in its ability to provide continuous security validation and quantifiable risk assessment. Organizations receive detailed reports showing which simulated attacks succeeded, which were blocked, and which went undetected, along with specific remediation guidance for identified security gaps. This enables security teams to prioritize their efforts based on actual attack scenarios rather than theoretical vulnerabilities.
BAS also facilitates purple team operations by providing shared visibility between offensive and defensive security teams.
BAS vs Proactive Product Security
Breach & Attack Simulation (BAS) differs fundamentally from proactive product security in its focus, scope, and timing within the security lifecycle.
Scope and Focus Differences
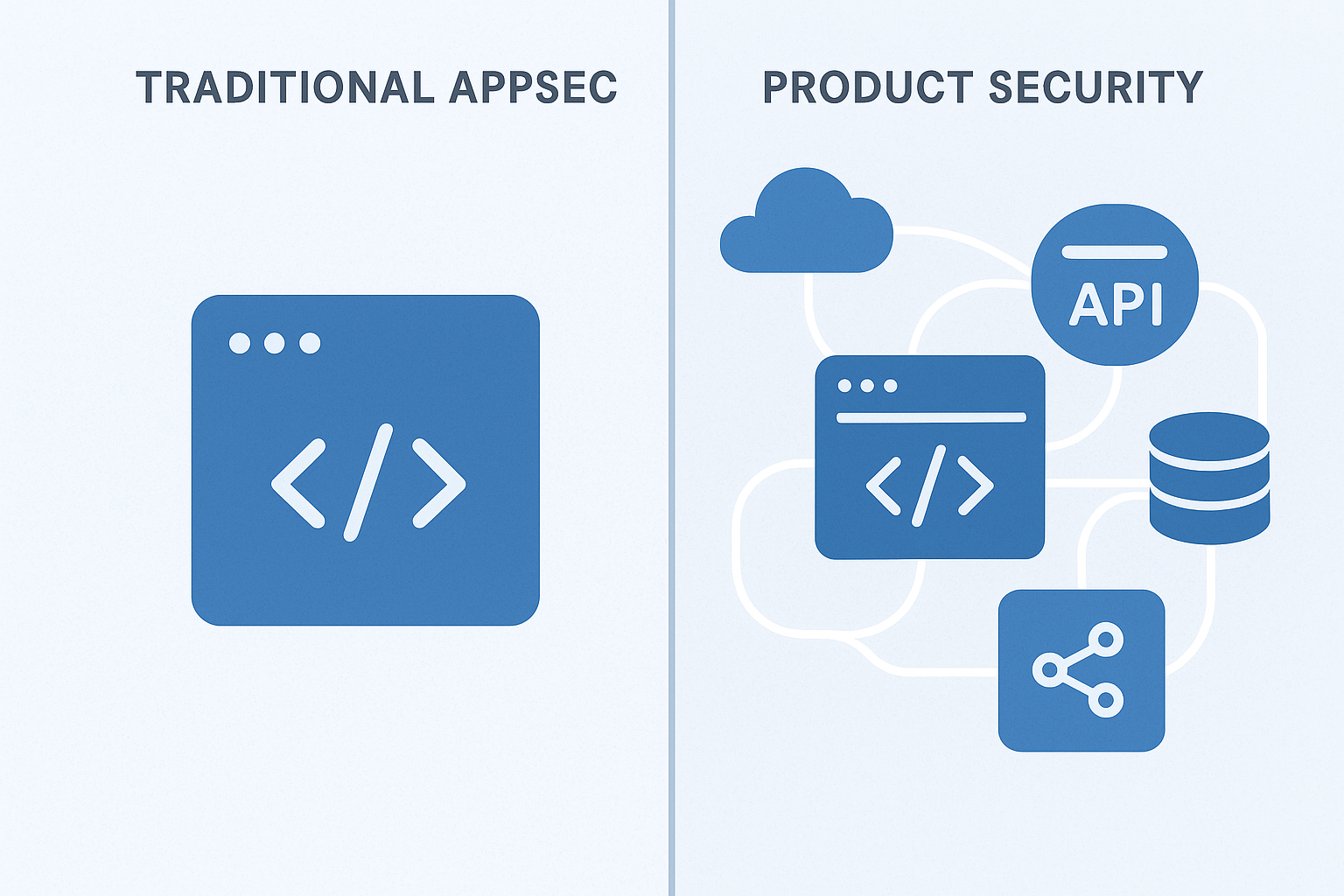
BAS is a broad security practice that tests an organization’s entire existing security controls and detection capabilities by simulating attacks against overall infrastructure and systems. Proactive product security, on the other hand, is product-focused and embeds security measures directly into products during their design, development, and deployment phases. Aspects of proactive product security include threat modeling, AppSec validation, and product red-teaming.
Simulation vs Real Asset Testing
BAS is a simulation of the actual asset. Although implementations may vary, typical BAS solutions have two components - an attacker module and a target module. The target module runs alongside the enterprise assets and has similar security controls as the real enterprise assets. The attacker component simulates attacks on the target module and based on those attacks reports what has succeeded and what has not.
Proactive Product Security, in contrast, looks at the actual enterprise assets and finds the actual issues.
Synergistic Integration
The output of BAS assessments—including identified security control gaps, undetected attack techniques, and validated defensive capabilities—can be strategically fed into pentesting or red teaming AI agents to enhance their attack planning and targeting. This integration allows AI-driven offensive security tools to focus their efforts on areas where BAS has identified potential weaknesses or blind spots, creating a more comprehensive and data-driven approach to security validation that combines continuous automated testing with targeted human-led or AI-enhanced adversarial assessments.