· Appaxon Team · insights · 2 min read
What is Continuous Threat Exposure Management (CTEM)?
Continuous Threat Exposure Management (CTEM) is a comprehensive cybersecurity framework identified by Gartner that enables organizations to continuously and consistently evaluate the accessibility, exposure, and exploitability of their digital and physical assets.
Continuous Threat Exposure Management (CTEM) is a comprehensive cybersecurity framework identified by Gartner that enables organizations to continuously and consistently evaluate the accessibility, exposure, and exploitability of their digital and physical assets. Rather than relying on periodic vulnerability scans and compliance-driven security assessments, CTEM establishes an ongoing process of discovery, prioritization, validation, and mobilization to address security exposures across the entire organizational attack surface.
This approach recognizes that modern threat landscapes are dynamic, with new vulnerabilities, misconfigurations, and attack vectors emerging constantly.
The Five-Stage CTEM Framework
CTEM operates through five key stages:
- Scoping - defining what needs protection
- Discovery - identifying all assets and exposures
- Prioritization - focusing on the most critical risks
- Validation - testing actual exploitability
- Mobilization - coordinating remediation efforts
This methodology shifts security teams away from reactive patching of theoretical vulnerabilities toward proactive management of actual threat exposures that could be exploited by real attackers. By emphasizing continuous assessment and business-risk alignment, CTEM helps organizations focus their limited security resources on exposures that pose genuine threats to business operations and critical assets.
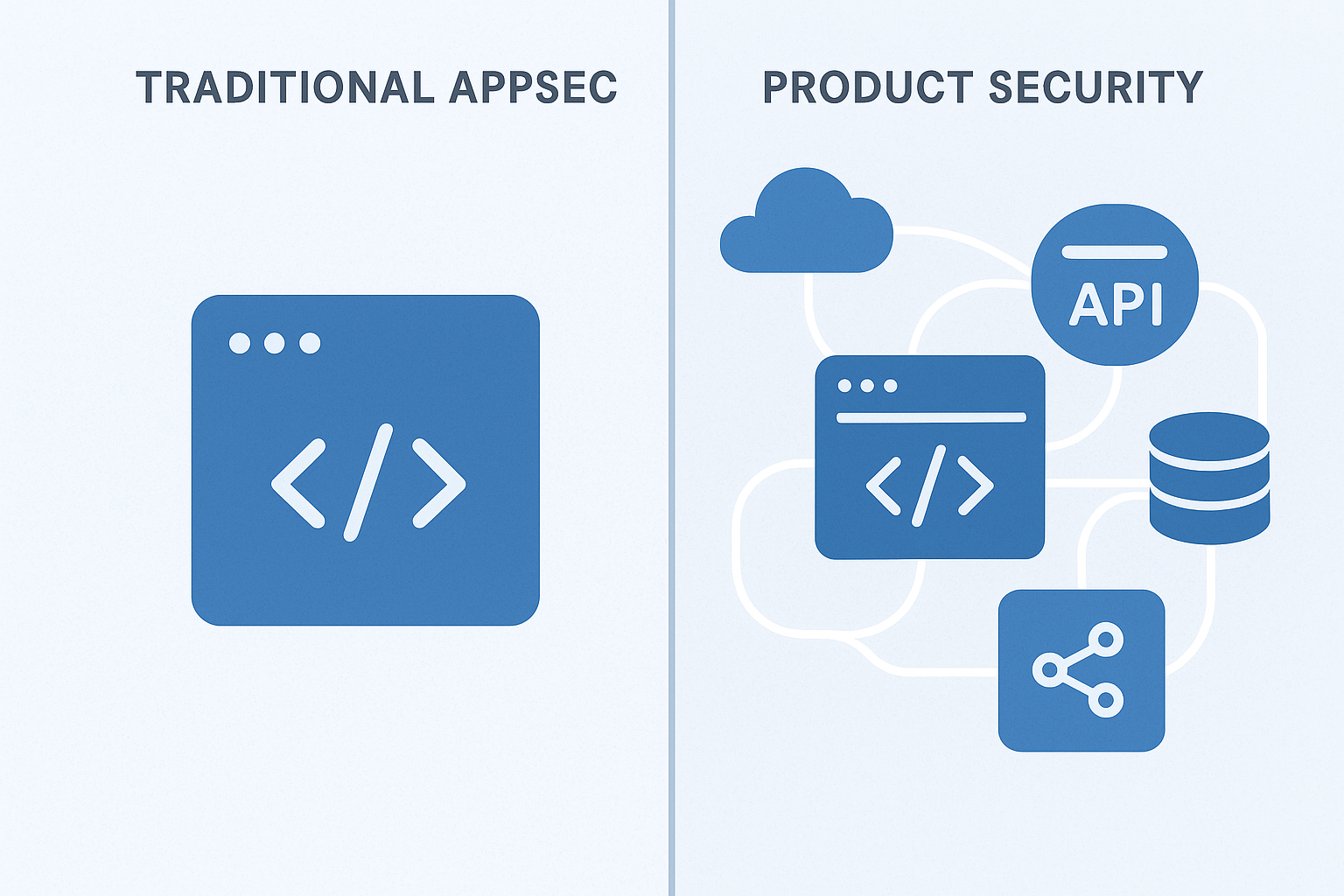
CTEM vs PTEM: Understanding the Relationship
Product Threat Exposure Management (PTEM) is a specialized application of CTEM principles that specifically focuses on software products and applications. While CTEM addresses the entire organizational attack surface—including infrastructure, networks, endpoints, cloud environments, and physical assets—PTEM narrows this scope to the complex ecosystem of modern software products with their dependencies, integrations, and runtime behaviors.
PTEM essentially applies CTEM’s continuous discovery, prioritization, and validation methodology to the unique challenges of product security, where applications are composed of numerous interconnected components, third-party services, and dynamic configurations. In this sense, PTEM represents a product-centric implementation of CTEM’s broader organizational security exposure management framework.
The Shift from Reactive to Proactive
The fundamental value of CTEM lies in its departure from traditional reactive security models. Instead of waiting for vulnerabilities to be discovered and then scrambling to patch them, CTEM provides a structured approach to understanding and managing the continuously evolving threat landscape. This proactive stance is essential in today’s environment where threat actors are increasingly sophisticated and the attack surface is constantly expanding through digital transformation initiatives.