· Appaxon Team · blog · 3 min read
Practical Approaches to Implement Product Security
Building on the fundamental differences between traditional application security and comprehensive product security, this post provides a practical roadmap for organizations ready to make the transition.
In our previous blog post, we explored the fundamental differences between traditional application security and comprehensive product security, highlighting why modern organizations need to think beyond code-level vulnerabilities. As we discussed, product security encompasses the entire ecosystem—from infrastructure and configurations to third-party integrations and operational environments—that traditional application security approaches often overlook.
Building on that foundation, this post provides a practical roadmap for organizations ready to make the transition. When your organization decides to adopt product security, it’s not about throwing away established application security measures. Rather, it’s about extending them so practitioners can assess and mitigate risks that traditional tests might miss.
Below are three steps that can help security and product teams align under one comprehensive framework:
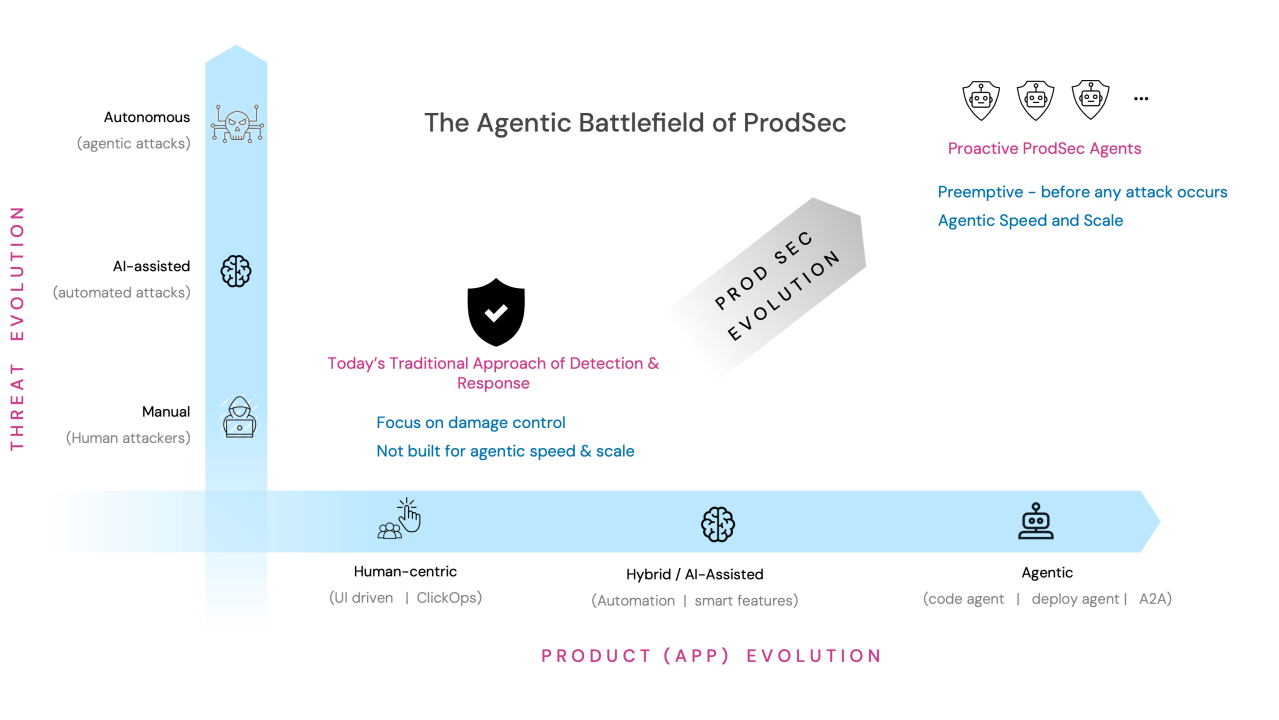
Step 1: Adopt a Continuous (and Preemptive) Exposure Mindset
While vulnerability scanning and penetration testing remain crucial, they often happen in snapshots—quarterly or on fixed schedules. This leaves gaps where new exposures can emerge undetected. A continuous mindset ensures real-time or high-frequency checks. Some teams add adversarial exposure validation (AEV) techniques that simulate real-world attacks across the product environment (not just the application code) to provide evidence of how an attacker might gain entry, pivot laterally, or escalate privileges.
Leading experts confirm that AEV, integrated with regular Continuous threat exposure management (CTEM), helps teams prioritize which vulnerabilities truly matter in a product context—rather than racing to patch every possible flaw on a long vulnerability list. This helps security teams focus on misconfigurations or design gaps that are genuinely exploitable.
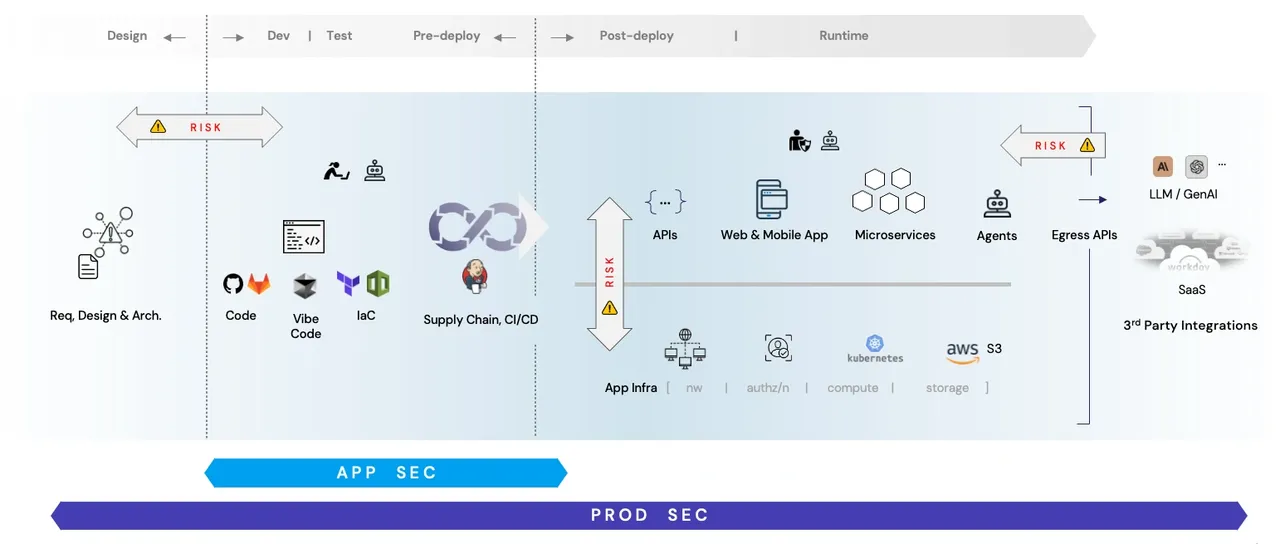
Step 2: Integrate Across the Product Lifecycle
Product Security is not a single-phase activity. The following checkpoints can help embed it seamlessly:
Planning/Design
Incorporate threat modeling during design sprints. This includes identifying any third-party libraries, external APIs, or hosting environments that come with special considerations.
Development
Train engineers on secure coding, but also ensure they know how to handle dependencies, configurations, and product interactions. Automated scanning tools can be extended to detect infrastructure or deployment misconfigurations in code (e.g., IaC templates).
Deployment and Operation
Real-time monitoring of actual environment states—network segmentation, endpoint policies, container configurations—and validating them against known threats. Automated moving-target defense strategies or dynamic obfuscation can also help here.
Maintenance/Updates
Each release or patch can shift the product’s exposure. Continuously reevaluate the threat landscape, especially if new features or integrations are introduced.
Step 3: Leverage the Right Tools, Techniques, and Frameworks
Practitioners looking to gain coverage across the product’s entire ecosystem can leverage an array of newer technologies:
Exposure Management Platforms
Extended vulnerability and asset mapping that goes beyond just code scanning, shining a light on everything from external attack surfaces to misconfiguration risks.
Adversarial Testing Solutions
Tools that automatically replay or simulate attack scenarios (e.g., pivoting across microservices, chaining vulnerabilities) to demonstrate how an attacker could move through the product stack and harm the environment.
Red-Teaming & PenTesting
Ensure that the product is thoroughly tested using red-teaming and pentesting techniques. These help demonstrate how a product weakness can be actually exploited by hackers.
Threat Modeling and Prioritization
Combine the above data with frameworks that rank exposures by potential impact on actual business processes, so the development and security teams know which issues to fix first.
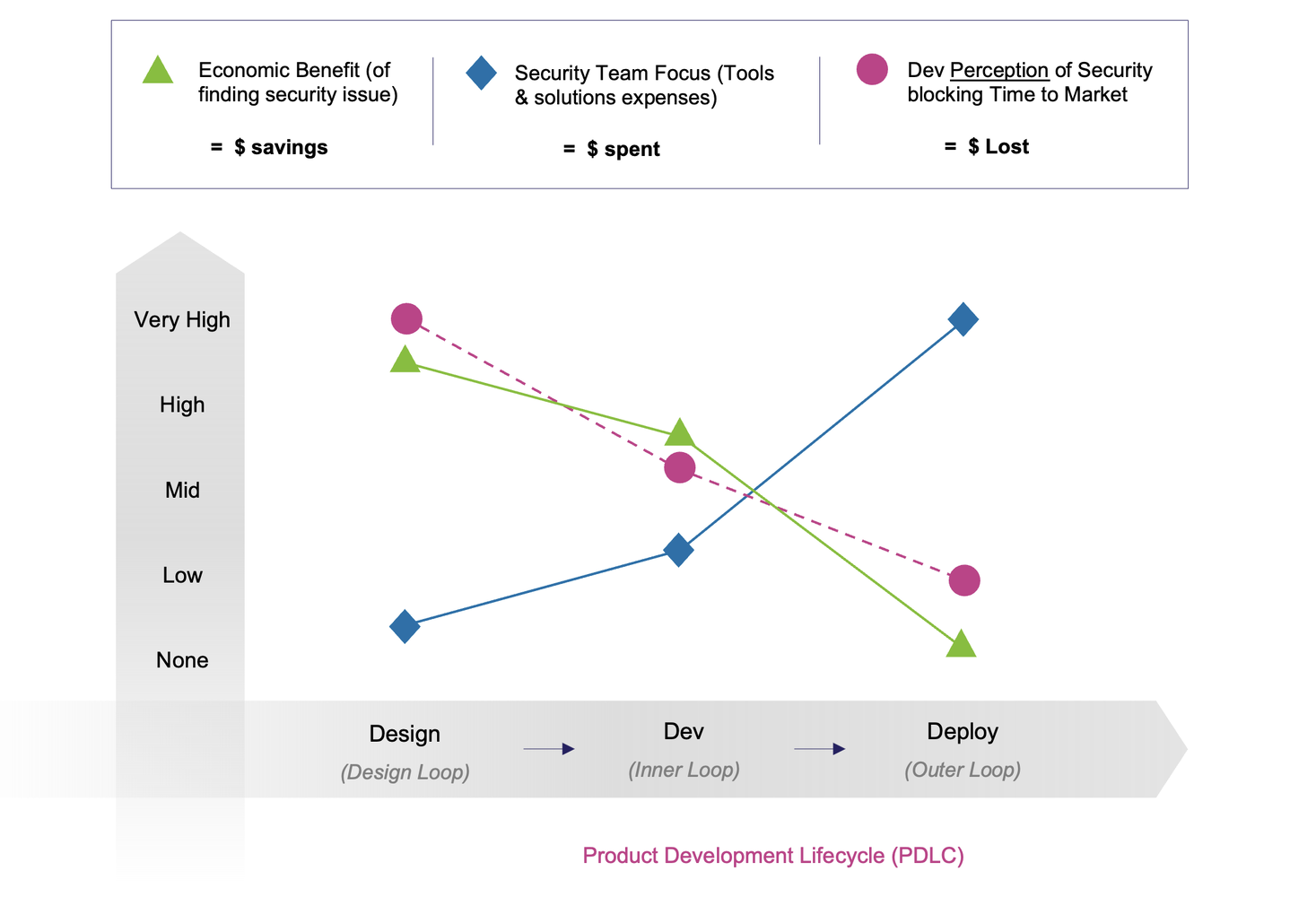
By adopting these capabilities, product teams can effectively move from reactive scanning to preemptive detection and mitigation—a shift many analysts see as critical for modern security strategies.