· Appaxon Team · blog · 4 min read
Product Security: Why AppSec alone is no longer enough
As software architectures have evolved into complex ecosystems, traditional application security approaches that focus primarily on code-level vulnerabilities are insufficient to address the comprehensive product threat landscape.
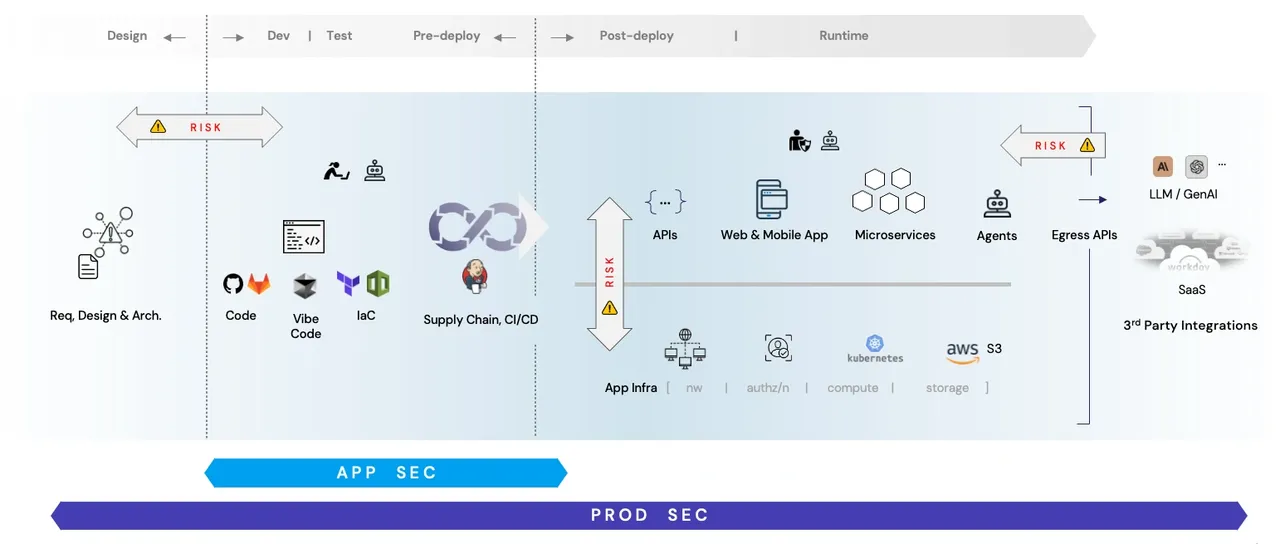
Securing software applications has always been a cornerstone of cyber security. This is because applications have direct access to and control over the enterprise crown jewel, i.e. enterprise data. However, as software architectures have evolved into complex ecosystems comprising microservices, infrastructure-as-code, third-party usage (e.g. SaaS and GenAI providers), and app-infrastructure components, traditional “application security” (“AppSec”) approaches that focus primarily on code-level vulnerabilities are insufficient to address the comprehensive product threat landscape.
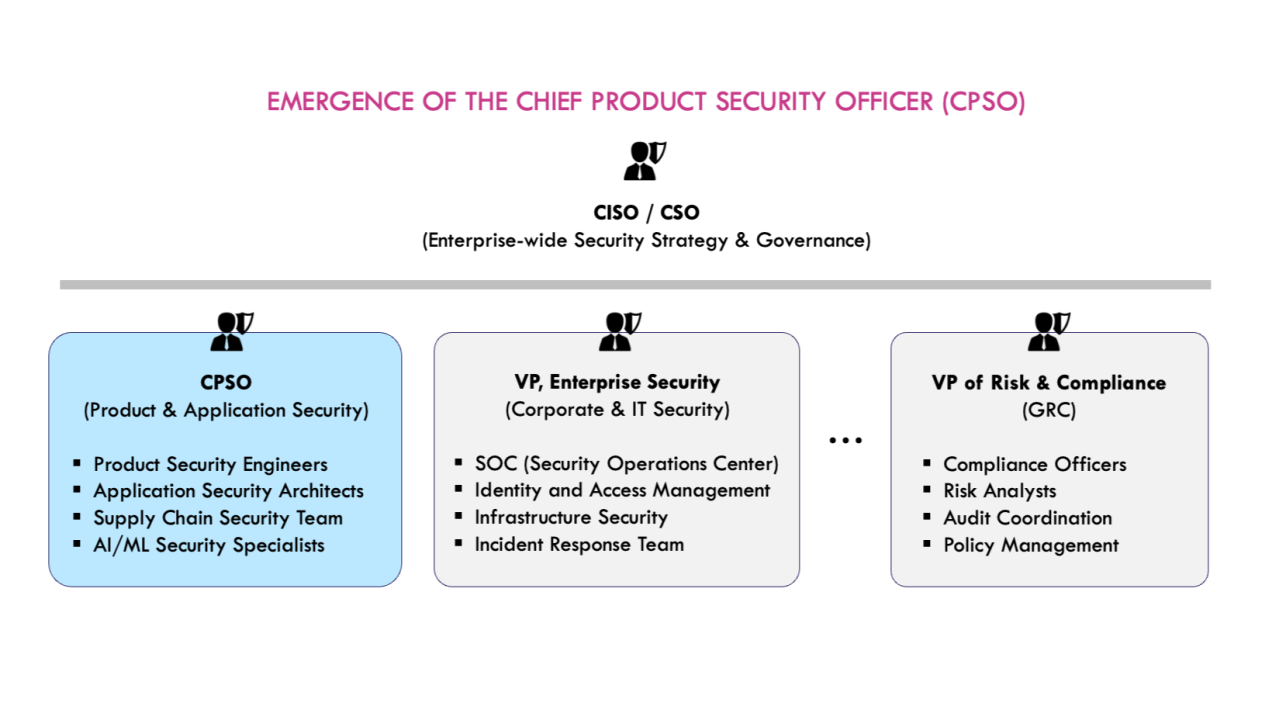
Forward-thinking CISOs and security leaders are now broadening their scope to look at the overall “product” in all its complexity — an evolution often referred to as “product security” or “ProdSec” in short.
What Is Product Security? How Is It Different From Traditional Application Security?
Application security typically focuses on safeguarding code bases through scans, ensuring secure-coding best practices, testing for application vulnerabilities (XAST), analyzing open-source composition (SCA), etc. More recently, it is being extended to also sometimes include software bill of materials (SBOMs) and supply chain security (“SSCS”) components. While absolutely critical, that view is limited to what happens within the boundaries of the application development pipelines.
Product Security, on the other hand, assumes a more holistic view and looks at the entire lifecycle of an application. A “product” isn’t just code; it’s also deployment configurations, data flows, cloud dependencies, product threat models, web of APIs, and third-party usage. The exposure a product faces, in addition to the code vulns — and the corresponding risk — extends into areas such as:
Deployment Complexity
When you ship an application across multiple environments, from on-premises installations to public cloud, each environment (Kubernetes, cloud networks, security groups, or object stores such as AWS S3) introduces its own potential exposures.
Risk from Third-Party and LLM Integrations
In an interconnected digital ecosystem, products rely on 3rd party SaaS services. More recently, however, there is increasing usage of LLMs (Large Language Models) and other generative AI providers - that offer weak links if left unchecked.
Platform Security and Access Controls
The underlying platforms that host and run applications are integral parts of the product ecosystem. Proper identity management, role-based access control (RBAC), privilege management, and secure service-to-service authentication are critical components that extend beyond the application code itself. Weaknesses in these areas can compromise the entire product, regardless of how secure the code base might be.
A Shift to a Product Mindset is a Must
Consider a simple SaaS app that integrates with multiple SaaS providers using APIs. If the product’s core code is secure, but one payment API is vulnerable to replay attacks, the entire “product” is at risk—even though the breach might not directly exploit the application code itself.
Consider another example where the application business logic is flawed and insecure, and the necessary compensating controls are put in place to mitigate the risk. Focusing only on AppSec would call this out as a critical risk, whereas when you look at it holistically from a ProdSec lens, and take into account the controls in place, the risk is not as high.
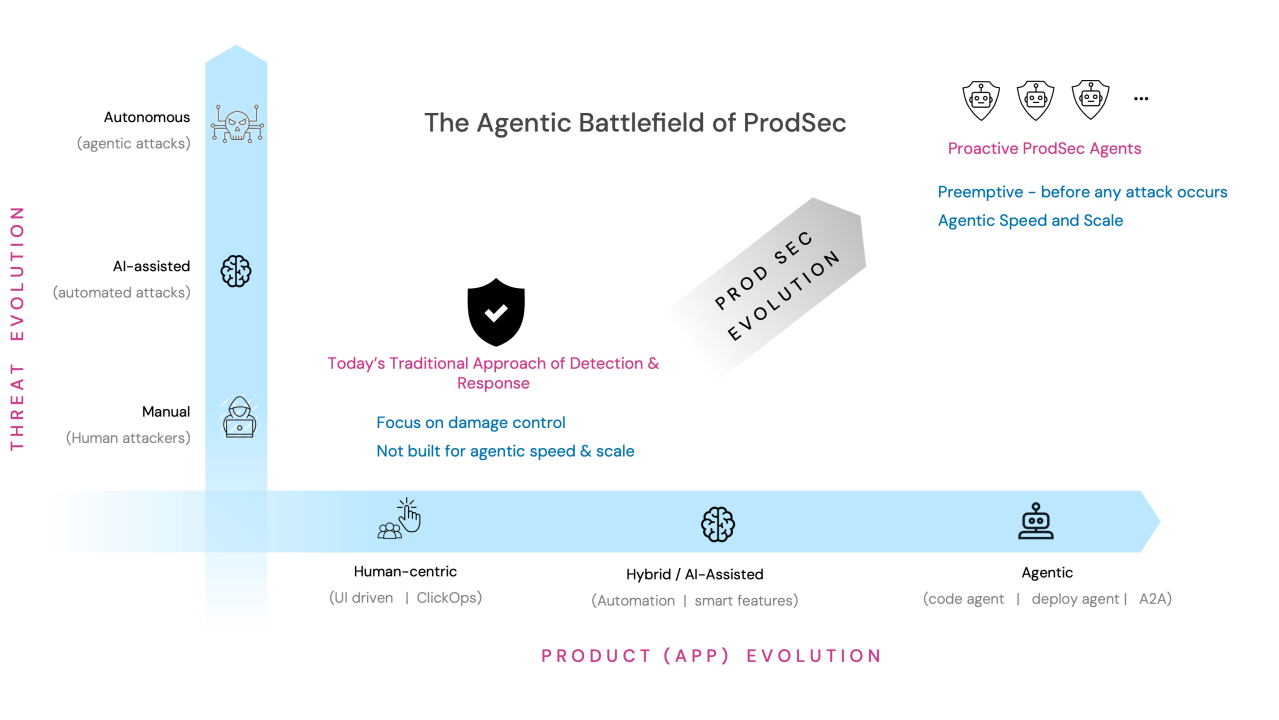
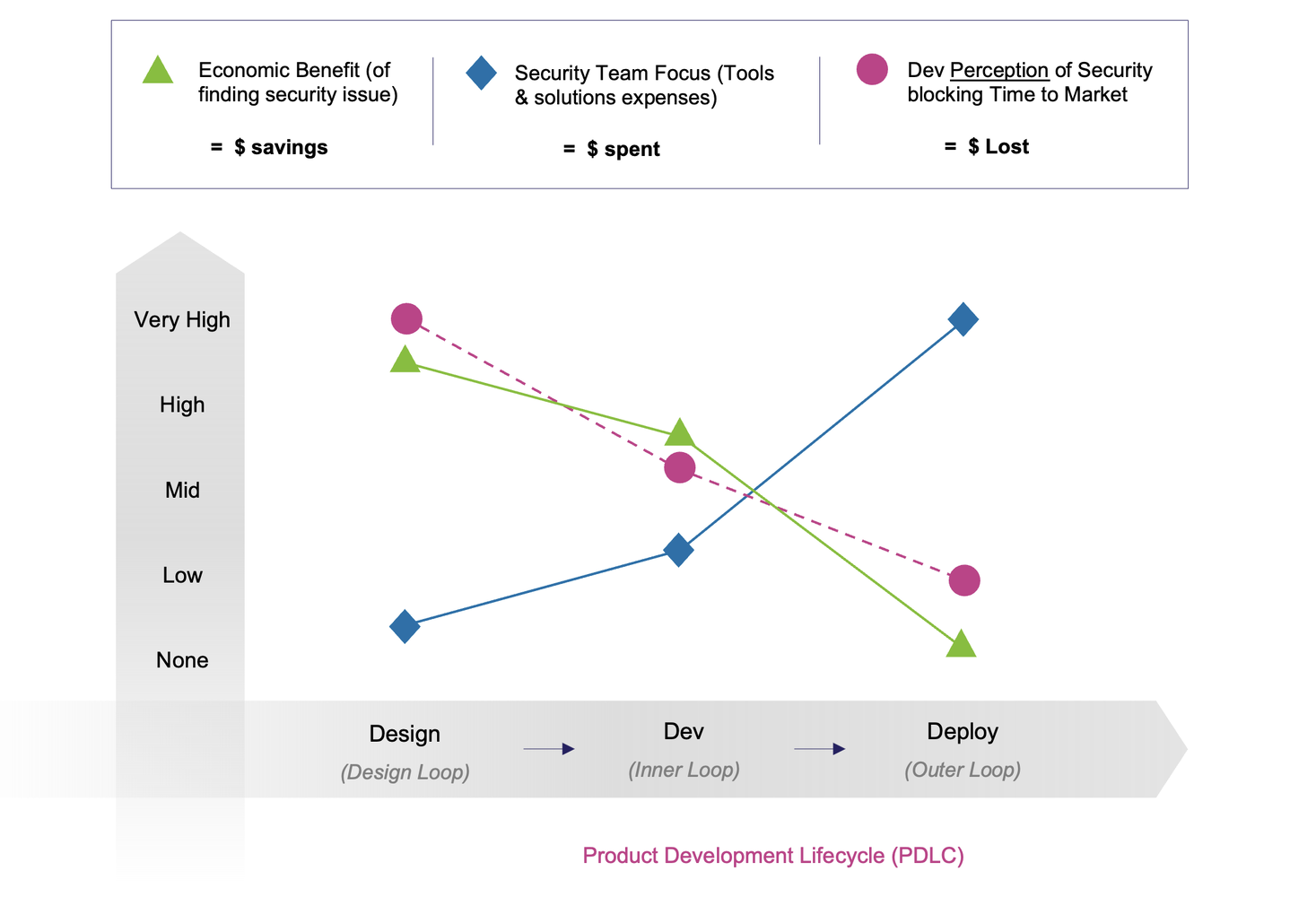
This is why we need to shift our mindsets from application security to product security. Industry analysts have recently emphasized that a broader view — looking at every possible point of exposure — helps security and product teams focus on actual weaknesses rather than theoretical CVEs and code flaws. This shift from “application security” to “product security” ensures that teams see the entire picture of the threat exposure.
Businesses Must Evolve
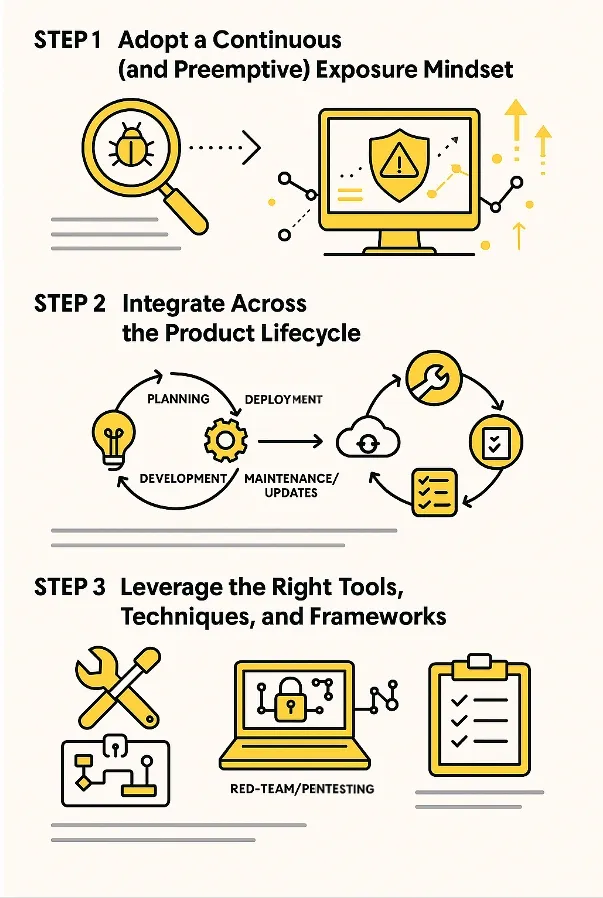
In the current threat landscape, it’s no longer sufficient to treat security as either ‘shift left’ or ‘protect right’. Instead, businesses must recognize that security should extend across the entire product lifecycle. From end-to-end product threat models, to strategic compensating controls, to mitigating external exposure from service integrations, product security offers a far more inclusive view — one that helps identify genuine, real-world risks early and comprehensively.