· Appaxon Team · insights · 2 min read
What is Product Threat Exposure Management (PTEM)?
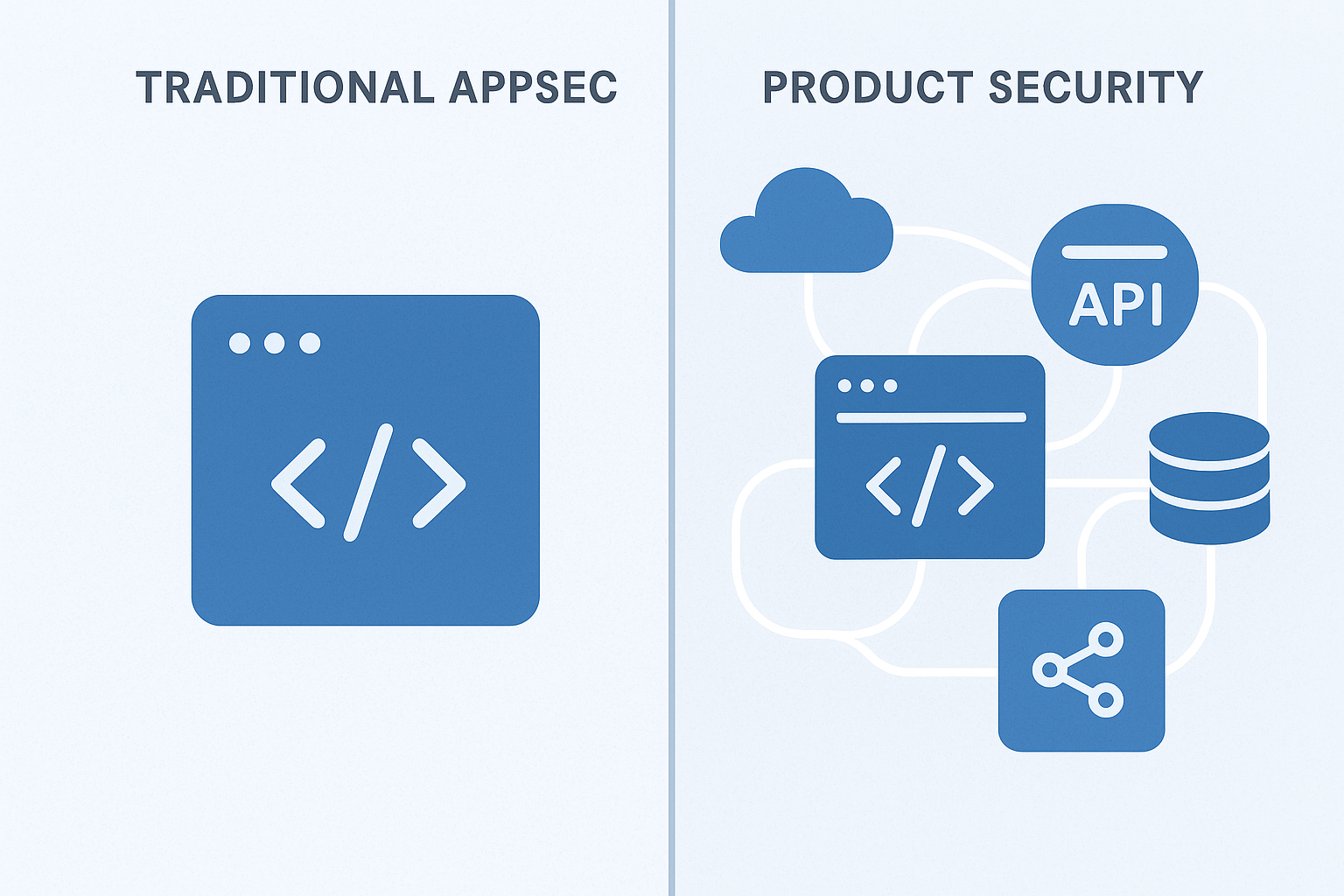
Product Threat Exposure Management (PTEM) represents a fundamental shift from traditional application security to a holistic approach that treats software as complete products rather than isolated codebases.

Product Threat Exposure Management (PTEM) represents a fundamental shift from traditional application security to a holistic approach that treats software as complete products rather than isolated codebases. Unlike conventional vulnerability management that focuses on individual CVEs and theoretical risks, PTEM continuously identifies, prioritizes, and mitigates actual threat exposures across the entire product ecosystem—including all dependencies, integrations, APIs, and runtime environments that make up modern applications.
Beyond Traditional Vulnerability Management
PTEM encompasses the full spectrum of product components that create attack surfaces: open-source libraries, supply chain dependencies, third-party SaaS integrations, AI/ML models, microservices, cloud configurations, and API endpoints. It moves beyond static code analysis to provide real-time visibility into how these components interact, what data they access, and how vulnerabilities in one area could cascade through the entire product.
This approach recognizes that today’s applications are dynamic, interconnected systems where a weakness in a single dependency or misconfigured integration can compromise the entire product.
Business-Aligned Risk Management
The core value of PTEM lies in its ability to provide actionable, risk-based insights that align with business impact rather than generating noise from theoretical vulnerabilities. By continuously monitoring the actual threat landscape and mapping it to specific product components, PTEM enables security teams to focus on exposures that pose real risk to their products and customers.
This proactive, product-centric approach is essential for organizations building at the speed and scale of modern development, where traditional reactive security measures simply cannot keep pace with the complexity and velocity of product evolution.
Relationship to Product Security
PTEM is a specialized capability within the broader Product Security discipline. While Product Security encompasses the entire security lifecycle—from secure design and threat modeling to security testing, compliance, and incident response—PTEM specifically focuses on the continuous detection and management of runtime threat exposures.
Product Security establishes the foundation through secure development practices and architectural decisions, while PTEM provides ongoing operational visibility into what’s actually at risk in production. Together, they create a comprehensive approach where Product Security builds security into products from the ground up, and PTEM ensures that security posture remains strong as products evolve, integrate new components, and face emerging threats in real-world environments.