· Appaxon Team · blog · 6 min read
Proactive: The Right Approach to Product Security
In an increasingly agentic battlefield, the traditional security paradigm of detecting a threat and then responding to it fundamentally remains a losing proposition.
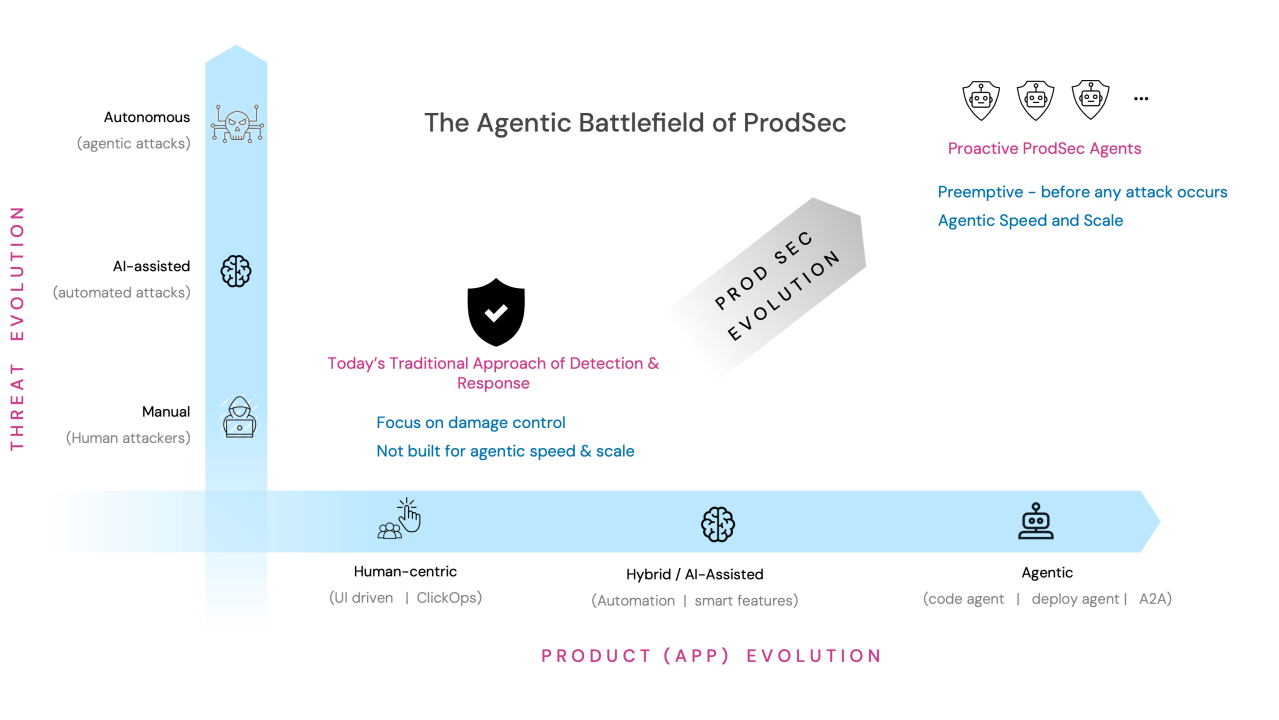
Software products and applications are increasingly moving towards an agentic world - whether it is code being written using agents (Cursor, Windsurf, etc.), deployment of apps using agents (Vercel, etc.), or communication between agents (MCP, A2A protocols, etc.). Meanwhile, bad actors are equally using agentic approaches for malicious activities. Agentic attacks have the capability to continuously learn from defensive responses and adapt their strategies in real-time.
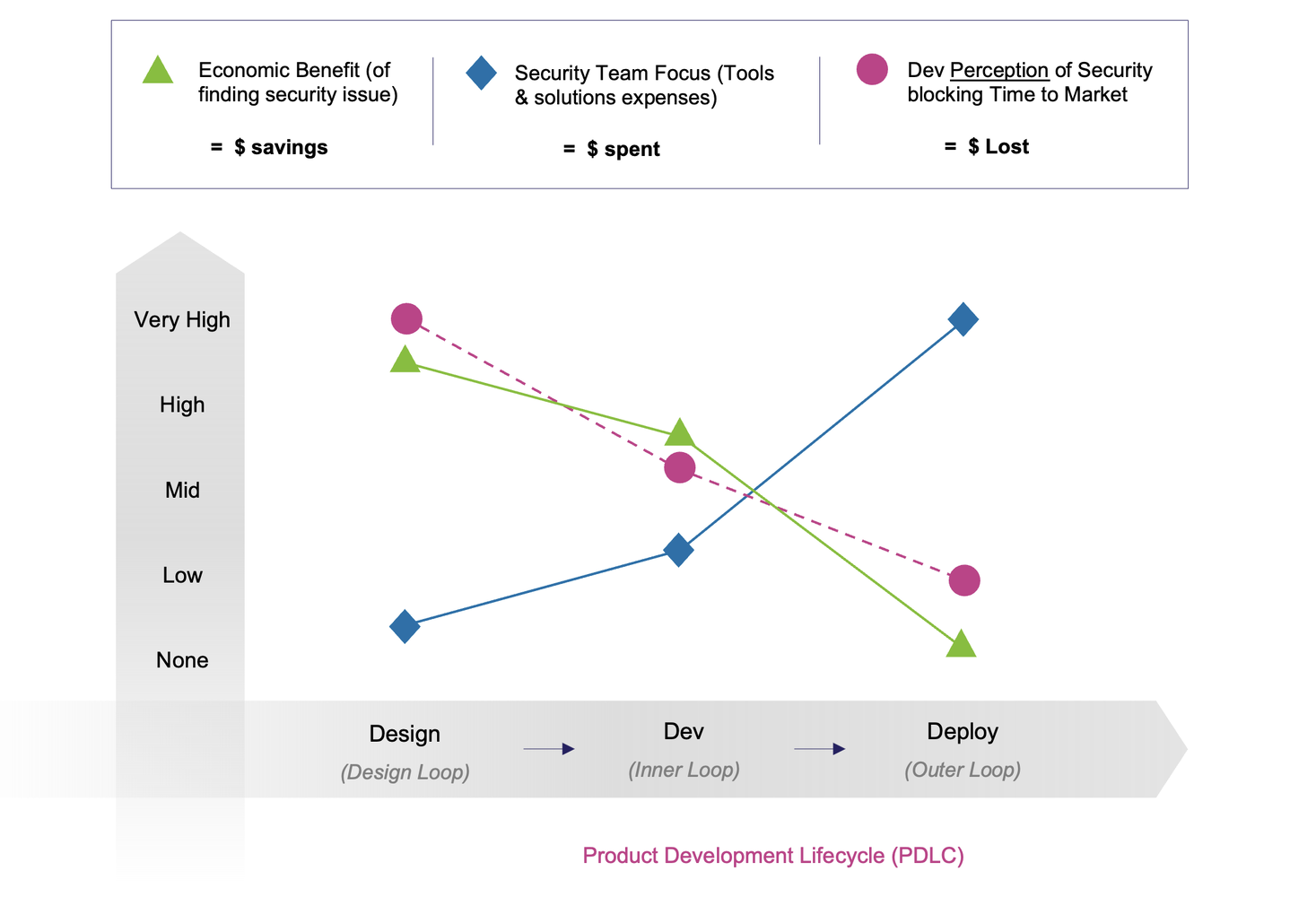
In this ‘Agentic battlefield’, the traditional security paradigm of detecting a threat and then responding to it, fundamentally remains a losing proposition. While absolutely essential to prevent a breach from doing further damage to the software product or application, it’s too late. By the time a breach is detected, damage has already occurred, and all you are left with is damage-control. Remember that the earlier you find an issue in the product lifecycle, the less it costs. According to IBM’s 2024 Cost of a Data Breach Report, the average cost of a single data breach is $4.88 million.
Reactive Security Falls Short
The limitations of current reactive security approaches become even more apparent in today’s threat landscape when we consider the following:
1. AI-Powered Agentic Attacks
Threat actors are increasingly leveraging AI and agentic approaches, creating an “agentic battlefield” that operates at AI speed and scale. This evolution means that defenders are increasingly facing adversaries that operate 24/7 with superhuman speed and precision, further highlighting the limitations of traditional reactive security approaches that rely on analysis and incident response. According to Gartner, “The growing weaponization of AI by threat actors is increasing pressure on detection and response strategies that are already lagging.”
2. Attacker-Defender Asymmetry
Defenders need to protect all potential entry points for products, whereas attackers need only find a single vulnerability. This asymmetry makes purely reactive strategies fundamentally unsustainable.
3. Product Complexity
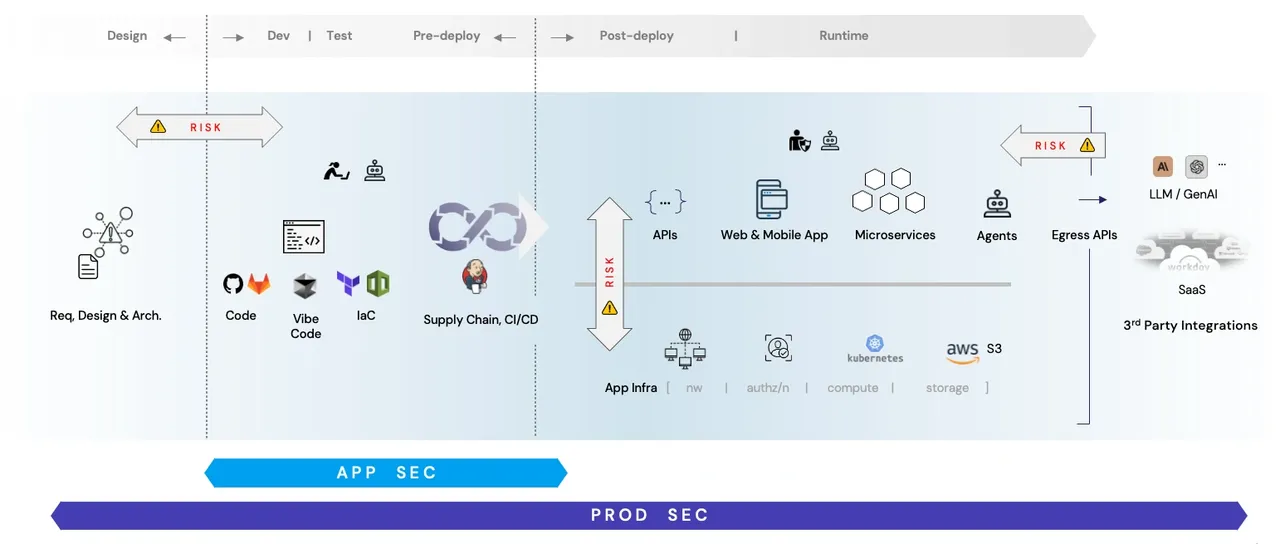
As we explored in our previous blog on Product Security, modern applications have evolved far beyond simple code bases into complex ecosystems comprising microservices, infrastructure-as-code, third-party services, and numerous integrations. As this expanded “product” grows more complex, and the attack surface expands significantly, comprehensive monitoring and detection become increasingly difficult.
4. Threats from Next-Gen LLM-Based Apps
There is a proliferation of AI within the enterprise apps, where LLMs (Large language models) and Generative AI models are extensively being used for their implementation. These new and next-gen apps create new and some unknown types of risks and attack vectors (prompt injection, goal hijacking, guardrail bypass, app infra attack, etc.). Can reactive solutions adapt to this changing product risk?
5. App Proliferation with ‘Vibe Coding’
The rise of “vibe coding” - where developers rapidly create applications using AI assistants, code generation tools, and low-code/no-code platforms - will result in an exponential increase in the number of apps, and hence unprecedented levels of security risks in the form of hidden technical debt (because of generated code), supply chain complexity (with increasing use of LLM’s trained on open source code), and so on. All this puts tremendous amounts of strain and burden on the reactive and detection-based security systems, which are already struggling with the lack of expertise in defending AI-generated code patterns and products.
The Case for Proactive (or Preemptive) Security
We need a fundamental shift in the way we think about product security. Rather than waiting for attacks to materialize, we should preemptively find issues and weaknesses within the software products and applications, and proactively remediate them. Proactive (or pre-emptive) cybersecurity, therefore, represents this fundamental shift in how we approach digital defense. The idea is to think like an attacker, not like a scanner.
According to a recent Gartner report, “Product leaders who do not adopt preemptive security strategies into their roadmap in 2025 will begin losing clients in 2026. The reactive security model alone will not be sufficient to combat the need for more efficient practices coupled with the growing cyber AI arms race.” Gartner furthermore predicts that “By 2030, preemptive cybersecurity solutions will account for 50% of IT security spending, up from less than 5% in 2024, and replace traditional ‘stand-alone’ detection and response solutions as the preferred approach to defend against cyberthreats.”
From Concept to Action: Making Proactive Security Practical for ProdSec
When we look at the current security implementations, most of the solutions largely fall into two broad categories:
1. Proactive but Theoretical
Many “shift-left” security initiatives focus exclusively on the development and supply chain pipelines - running xAST scans and tests, SCA, SBOMs, SSCS, etc. While absolutely essential, these measures often identify theoretical vulnerabilities or issues, and therefore are the perceived risk of an application or product. As a result, many of the solutions are known to be riddled with false positives and a high noise-to-signal ratio. Additionally, many of these ‘AppSec’ solutions work in the development pipelines, without the comprehensive context of what can happen to a product when it operates in production environments.
2. Exploitation-Centric but Reactive
On the other end of the spectrum, detection and response strategies, such as ADR (app detection and response), IR (incident response), etc., focus on the actual risk of products but kick in only after a threat actor has already penetrated defenses. At this point, organizations are playing defense on the attacker’s terms.
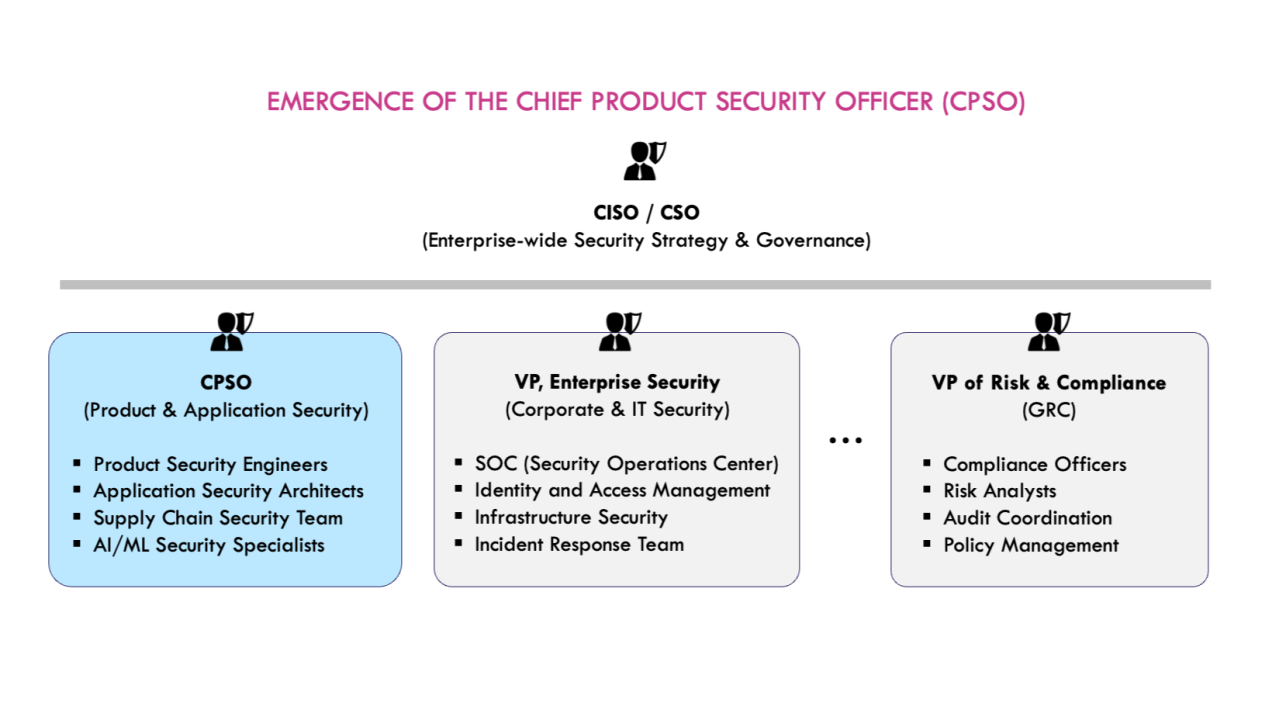
What is conspicuously missing, however, is a comprehensive security approach (i.e., ‘Prodsec’ focused) that is autonomous (and hence continuous), pre-emptive (rather than reactive), focuses on the real product risk (exploitation-centric), and proactively helps in remediation. This is where an evolution to an ‘Autonomous Proactive ProdSec’ becomes a crucial and viable strategy that complements the broader shift toward product security.
Practical Implementation Steps
To move from theory to practice, organizations should consider these initial steps:
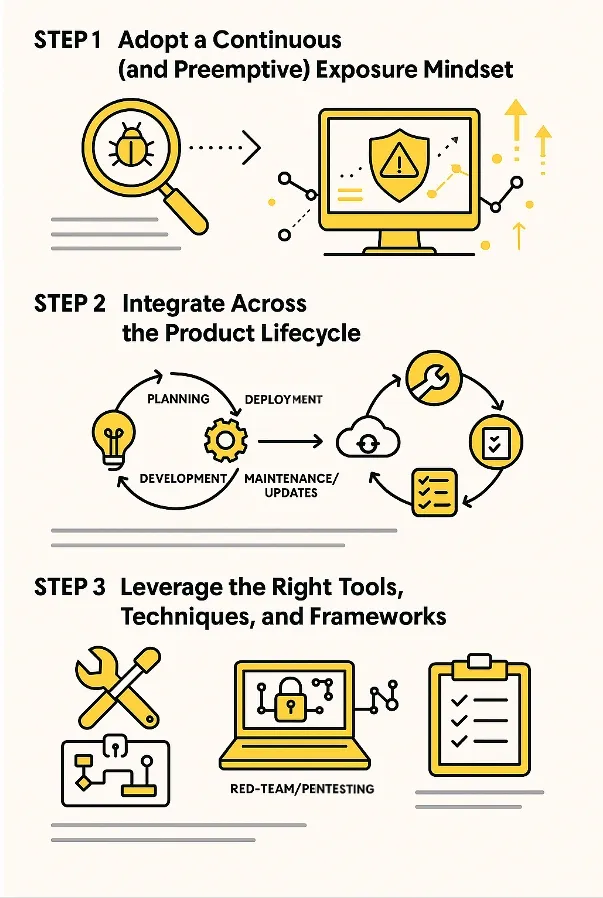
Prioritize High-Value Products: Identify high-value software products and applications (e.g. external-facing, sensitive-data-centric, business critical, etc.) within your product ecosystem that would benefit most from higher security standards.
Build Threat Models: Create product threat models to identify and map all potential threat scenarios for those products across the entire lifecycle.
Embed Threat Models in Development: Ensure that the threat models are actually incorporated by the dev teams while implementing and building the products.
Conduct Offensive Techniques: Engage in offensive cybersecurity activities on your product in your development pipelines and production environments. These could be pentesting/red-teaming, advanced cyber deception, advanced obfuscation, automated moving targets, etc.
Test Compensating Security Controls: Perform offensive exploitation-based tests of the compensating security controls and defenses that have been put in place to cover up for application weaknesses.
Foster Dev-Sec Collaboration: Ensure that the dev and security teams can collaboratively and proactively remediate issues found in these offensive tests, and not have disagreements on issue existence or priority.
Leverage Generative AI: Most importantly, leverage the reasoning power of generative AI models in solving your security challenges, and do not be apprehensive about them.
The Critical Question
As we (prodsec community) look to the future of product security, we must ask ourselves: How can we make proactive security not just theoretical but actionable for our business-critical products?
The answer will vary for each organization, but what’s clear is that the combination of comprehensive product security scope with proactive security techniques represents the most promising path forward in an increasingly hostile digital landscape.
Those who successfully bridge the gap between theory and action in proactive security will gain a significant advantage in protecting their products—and their businesses—from the next generation of cyber threats.